Firewall Policy Builder
Next Generation Firewalls are now the de-facto security gateways across your enterprise network – protecting your perimeter, data center and extranet from cyber-attacks targeting your IT assets.
Deploying new next-generation firewalls should result in better security posture with well-defined security policies, integration into the active directory for role-based access control along with application awareness and granularity. The reality is somewhat different – organizations are facing challenges in being able to translate the technical features and benefits of the next generation firewall into the real world.
In comes Firewall Policy Builder – we enable security teams to quickly and accurately lock down OPEN security firewall policies. Through real-time analysis, recommendation of firewall policies based on usage and generation of automated bulk configuration commands that are simply executed on the firewalls. Locking down open security policies on your next-generation firewall deployment is now made easy with firewall policy builder – allowing you to lock down in weeks rather than months or even years.
The firewall policy builder comes in different form factors – physical appliance, virtual appliance or as a SaaS cloud service to suit the needs of the organization.
"OPEN security policies on your enterprise firewalls is a common problem that many security practitioners can relate to. Whether it is deploying new cluster of NGFWs in your data center that never existed or you are inheriting a legacy firewall with OPEN security policies that has been the cause of audit failures."
Firewall Policy Builder is here to assist your organization meet compliance requirements by helping you “lock down” your high-risk OPEN security policies in real-time.
LOCK DOWN OPEN FIREWALL SECURITY POLICIES
We at Firewall Policy Builder are here to help organizations take on the challenge of optimizing their security effectiveness. An enormous amount of budget is spent every year in security technologies and products with the sole aim to protect critical assets from intrusion.
With all the focus centered around the technology and product deployed less emphasis is given to fine-tuning, enhancing and optimizing the configuration of the security products. 90% of organizations that have Next-Generation Firewalls and Intrusion Prevention Systems have ineffective security policies – not because they endorse it but due to the lack of visibility on what needs to be enforced.
At Firewall Policy Builder we will guide and help you drive security effectiveness through configuration optimization of NGFWs and NGIPS devices.
- Assists in locking down OPEN firewall security policies
- Reduces exposure from high-risk OPEN security policies
- Helps meet compliance requirement of granular security policies on need to know basis
- Assists in new NGFW firewall deployments in your data center where firewalls never existed
- Provides assistance and optimization when migrating from one firewall vendor to another
HOW IT WORKS
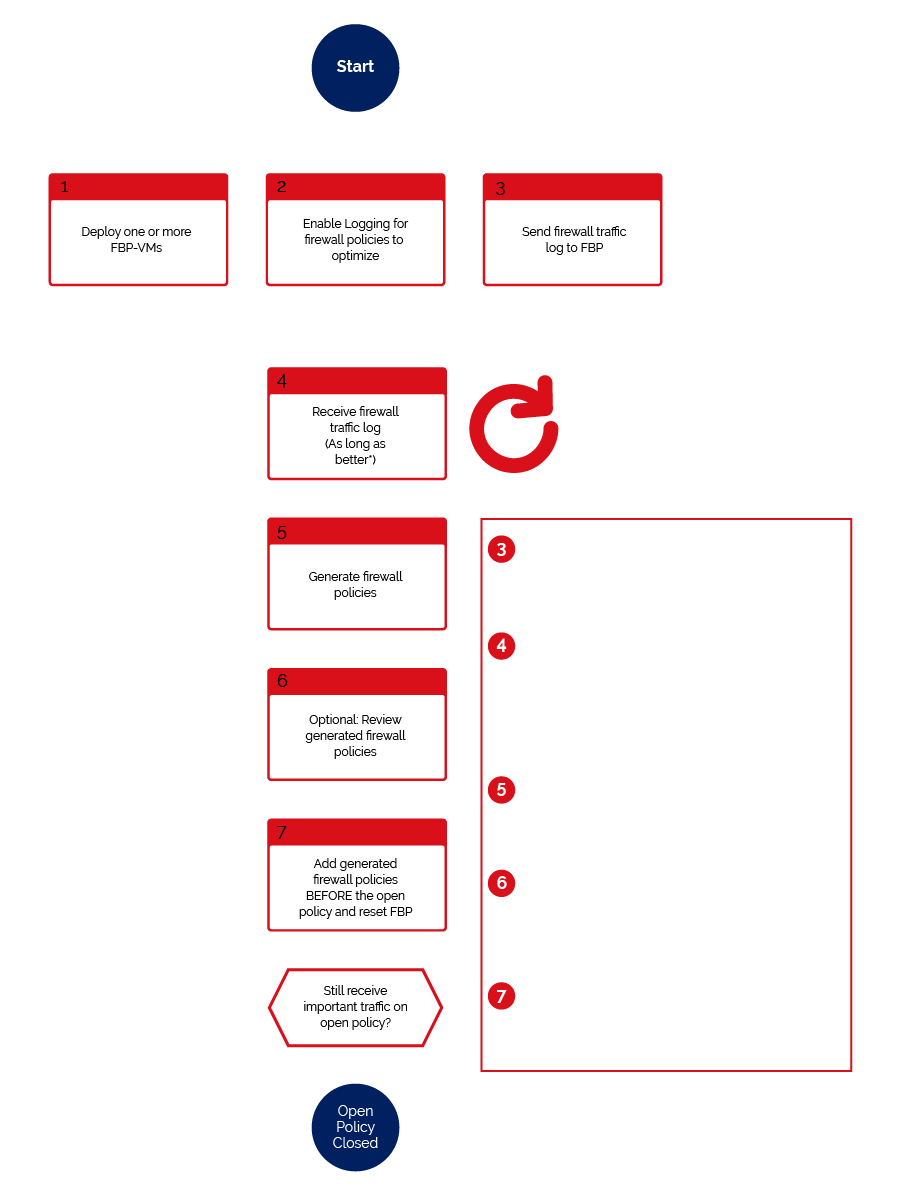
The appliance is installed at the organization’s management network.
The newly deployed next-generation firewall sends traffic logs in the form of SYSLOG to the firewall policy builder tool which performs real-time analysis and storing the communication flow matrix in a series of complex databases.
With custom developed advanced algorithms, the tool populates the database with the communication flow as the firewall continues to send traffic SYSLOG to the tool.
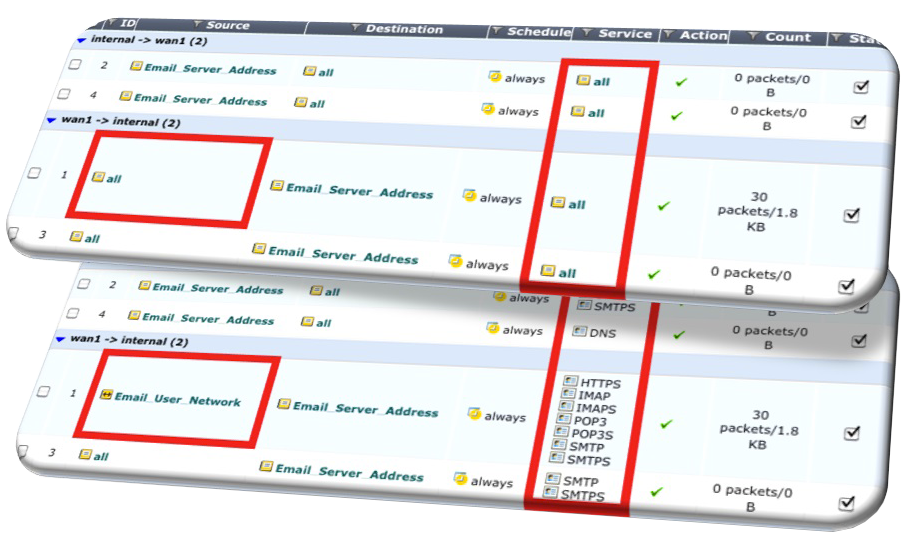
After sufficient time-span of a few weeks to capture sufficient traffic flow, that tool can then be instructed to the group, coalesce and combine traffic flow of similar characteristics. For example, ten source IP addresses communicating to the same destination IP address with five TCP and UDP ports are grouped into a single policy and single communication flow matrix.
Once grouped the firewall policy builder can then generate the CLI configuration commands of the grouped security policies in different formats.
Firewall policy builder supports various next-generation firewall technology vendors. Once the configuration commands are generated the IT department can simply copy and paste the configuration to the firewalls and apply the changes resulting in open security policies on firewalls being locked down in a short period of time.
TECHNICAL FEATURES
- Works with major NGFW vendors - Juniper Networks SRX and Fortinet FortiGate platforms
- REAL-TIME SYSLOG Engine parsing traffic logs for OPEN security policies
- Pre-Hardened Secure Database for SYSLOG data retention and normalization
- Advanced Grouping Algorithm of traffic flow SYSLOG data that are of similar characteristics
- Granular filtering of SYSLOG data to analyze interesting security policy IDs, security zones, ingress interface etc
- Automated one-click generation of consolidated security firewall policies configuration commands
- Automated configuration commands can be executed directly into the supported firewalls
- Integration with SIEM solution as a secondary SYSLOG forwarding destination
Professional Services
Our Professional Services team are experts in designing, deploying, implementing and migrating firewalls for enterprises of any scale and size. We offer multiple types of professional services engagement that is based on Firewall Re-Design and Optimization, Firewall Migration Service and Policy Clean-Up using Firewall Policy Builder as a tool to help your organization meet the challenges of firewall life-cycle management.
The Team
We believe in a diverse range of personel to bring technical skills,
thoughts, and ideas to the table.
SHAH H. SHEIKH
FOUNDER
Shah H Sheikh is the founder of Firewall Policy Builder, having also co-founded DTS Solution (www.dts-solution.com) a highly specialized information and network security consulting firm based in Dubai, UAE. He has the strategic vision, expertise, and experience to lead Firewall Policy Builder in the right direction.
Shah Sheikh has ample experience when it comes to firewall life-cycle management having worked for Juniper Networks and Fortinet prior to founding DTS Solution. Previously he was also responsible to lead a team of consultants and engineers for a system integrator providing managed security services that involved managing a vast number of firewalls – he also has held roles as a technical lead for the largest mobile operator in the UK to manage, operate and maintain their entire firewall estate.